What is Static Analysis? Boost Code Quality & Security
Think of static analysis as an expert proofreader for your code. It's an automated process that scans every line for bugs, security flaws, and style problems without ever actually running the program. It’s all about catching mistakes before they ever make it to print.
The Automated Code Proofreader
Imagine you're building a skyscraper. Long before the first steel beam is set in place, an architect pores over the blueprints. They're looking for structural weaknesses, design flaws, and anything that violates building codes. This crucial review prevents catastrophic failures and avoids hugely expensive changes down the road.
Static analysis does the exact same job for your software.
Instead of waiting for your program to crash to find a problem, static analysis tools read the source code directly—just like an architect reads a blueprint. They act as an automated code review, systematically checking your entire codebase against a set of rules to spot potential issues at the earliest possible moment.
This "pre-flight check" is fantastic at identifying a whole range of problems:
- Potential Bugs: It can find things like null pointer exceptions or unreachable code that would otherwise cause a crash in production.
- Security Vulnerabilities: It flags common security risks, like SQL injection possibilities or secrets you accidentally hardcoded into the source.
- Code Quality and Style: It helps enforce consistent formatting and coding standards across your team, making the code easier for everyone to read and maintain.
By flagging these issues before the code is even compiled, let alone tested, static analysis gives you a powerful first line of defense. It makes the entire development process faster, cheaper, and way more reliable.
It's no surprise that these tools are becoming more common, especially with the rise of cybersecurity threats and increasingly complex applications. The global market for static code analysis software hit around $1.2 billion in 2023 and is on track to reach nearly $2.6 billion by 2032. This growth shows just how essential automated analysis has become everywhere, from finance to healthcare. You can dig into these market trends and their drivers in various detailed industry reports.
Ultimately, getting a grip on what static analysis is all about is the first step toward writing cleaner, more secure, and more efficient code. It gives developers the power to fix mistakes on the spot, long before they have a chance to become full-blown production incidents.
The Real-World Benefits of Static Analysis
It’s easy to think of static analysis as just an automated proofreader for your code. And while that’s true, its real value shows up in the tangible improvements it brings to your team’s workflow and, ultimately, the final product. We’re talking about concrete gains in speed, security, and overall code quality.
The most obvious win is how much time and money it saves. Finding and squashing a bug during development is exponentially cheaper than dealing with it after a release. An issue caught by a static analysis tool takes a developer a few minutes to fix. That same bug, once live, can lead to hours of frantic debugging, emergency hotfixes, and frustrated customers.
This early detection becomes absolutely essential as your team gets bigger.
Enforcing Consistency and Quality at Scale
When you have multiple developers contributing to a single codebase, keeping everyone on the same page with styling and best practices can feel like herding cats. Static analysis acts as an impartial referee, automating the rules so everyone plays by them.
- Standardized Codebase: It ensures every contributor follows the same formatting rules, naming conventions, and structural patterns. The result? A predictable codebase that’s far easier for anyone on the team to jump into.
- Reduced Review Fatigue: Manual code reviews can easily get bogged down in nitpicky debates over style. By automating these checks, reviewers can skip the small stuff and focus their brainpower on the things that really matter, like logic and architecture.
This kind of consistency is the bedrock of a healthy development cycle. You can see how this philosophy ties into the bigger picture by exploring some continuous integration best practices that help teams deliver better results.
A Proactive Stance on Security
Perhaps the most critical benefit of static analysis is its role in security. In a world where vulnerabilities are constantly being discovered and exploited, waiting until the QA phase to look for security holes is a recipe for disaster. Static Application Security Testing (SAST), a crucial part of static analysis, acts as a vigilant guard right from the start.
By scanning for common vulnerabilities like SQL injection, cross-site scripting (XSS), or buffer overflows directly in the source code, static analysis helps you build security into your application from day one, rather than trying to bolt it on as an afterthought.
This “shift-left” approach to security has become fundamental to modern software development. It gives developers the power to find and fix potential threats long before the code ever sees a production server. At the end of the day, using static analysis isn't just about catching bugs—it’s about building faster, more dependable, and fundamentally more secure software.
How Static Analysis Works Behind the Scenes
To really get what static analysis does, it helps to pop the hood and see how these tools work their magic. Think of a static analysis tool as an expert architect reviewing a building's blueprints long before the first brick is laid. They don't need to see the physical building (the running program) to spot fundamental design flaws.
Instead, the process kicks off by translating your human-readable source code into a structured, machine-friendly format. This "blueprint" is usually an Abstract Syntax Tree (AST). An AST is just a fancy way of saying the tool breaks your code down into its core components and maps out the relationships between them. It creates a complete, logical picture of everything your program is supposed to do.
Once that map is built, the real inspection can begin.
Applying the Rules of the Road
With the AST in place, the static analysis tool starts applying a comprehensive set of "building codes"—a library of predefined rules—to hunt for issues. These rules cover everything from weak architectural patterns and security holes to simple stylistic slip-ups. This is where the core analysis happens, and it typically relies on a few key techniques.
- Pattern Matching: This is the most straightforward method. The tool scans your code for patterns that are known to be problematic, like calling a deprecated function or writing a loop that could run forever.
- Data Flow Analysis: This one's a bit more advanced. It actually tracks data as it moves through your application. It follows a variable from the moment it's created to every single place it's used, checking for problems like potential null pointer exceptions or making sure sensitive data isn't accidentally exposed.
- Taint Analysis: Think of this as a specialized form of data flow analysis built for security. It "taints" any input from a user as untrustworthy and then follows it to see if it ever gets used in a dangerous way—like in a database query—without being properly sanitized first.
Together, these techniques create a powerful, automated review process. They give developers a clear heads-up on potential issues, letting them fix structural problems, security risks, and common coding mistakes before a single line of code ever executes.
This infographic breaks down the core pillars static analysis supports, from squashing bugs to beefing up security.
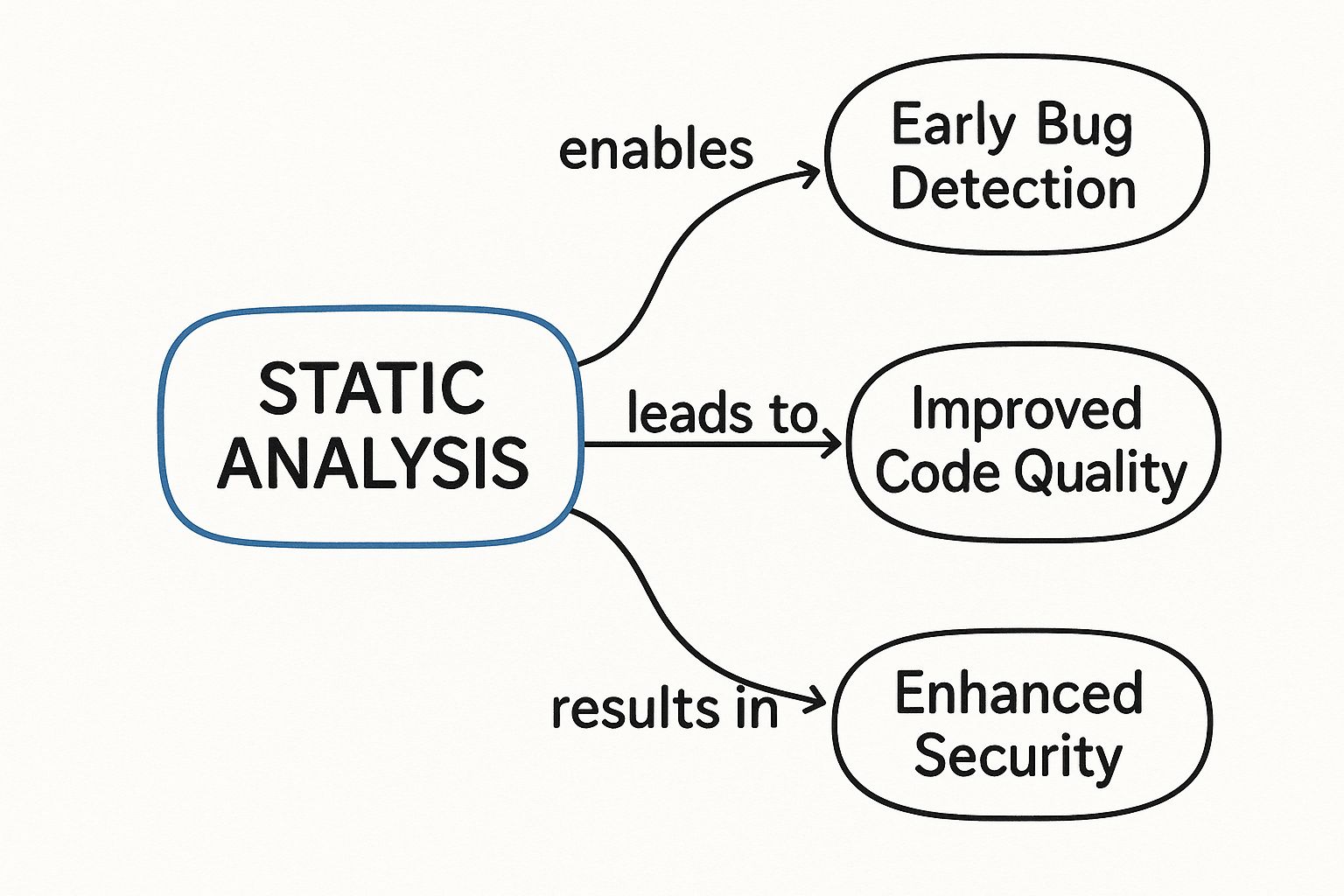
As you can see, these benefits all feed into each other. Spotting problems early directly leads to higher-quality code and much stronger security.
Weaving Analysis into the Workflow
The true power of static analysis is unleashed when it becomes an automatic, almost invisible part of your daily development routine. By plugging these checks directly into a Continuous Integration (CI) pipeline, teams create an automated quality gate.
Here’s how it works: a developer pushes new code, and the CI server instantly kicks off the analysis.
If any critical issues are flagged, the build can be failed on the spot, preventing flawed code from ever being merged. This immediate feedback loop is foundational to modern software development. To see how this fits into the bigger picture, you can learn more about what Continuous Integration is in our simple guide. This automated safety net ensures that code quality and security standards are enforced every single time, making the whole development process more efficient and reliable.
Choosing the Right Static Analysis Tool
With a sea of static analysis tools out there, picking the right one for your project can feel a bit overwhelming. The secret is to zero in on what you actually need. Are you trying to enforce a consistent code style, squash bugs before they see the light of day, or lock down your application's security?
The best tool for the job really depends on your tech stack and your primary goals. Let’s break down the main categories to help you figure out where to start.
Language-Specific Linters and Style Checkers
For most developers, the journey into static analysis begins with a linter. Think of these as lightweight, focused tools that are obsessed with enforcing coding standards, flagging common syntax mistakes, and keeping your codebase clean and consistent.
If you're working on a JavaScript or TypeScript project, you're almost certainly using a tool like ESLint to set rules for everything from variable declarations to comma placement. Python teams lean on tools like Pylint or Flake8 to make sure their code follows the official PEP 8 style guide. They’re fantastic for maintaining readability.
Linters are your first line of defense in the static analysis world, focusing squarely on style and syntax. To get the full picture, you can learn more about what linters are and why they're a foundational piece of the code quality puzzle.
This tight focus on consistency makes them a no-brainer for any modern development workflow, giving you instant feedback right inside your code editor.
Comprehensive Code Quality Platforms
Linters are great for keeping things tidy, but sometimes you need to bring out the heavy machinery. That's where comprehensive code quality platforms come in. These tools go way beyond style checks, diving deep to find tricky bugs, security vulnerabilities, and complex code quality issues across dozens of languages.
- SonarQube: This is a hugely popular open-source platform that gives you detailed dashboards on code smells, security hotspots, and test coverage. It becomes the central command center for your project's health.
- DeepSource: This tool plugs right into your version control system (like GitHub) to provide automated analysis. It doesn't just find problems—it often suggests the fixes for you.
Platforms like these are perfect for larger teams or companies that need to maintain high standards across a whole portfolio of projects from one unified place.
Security-Focused SAST Tools
When security is your top priority, you need to look at dedicated Static Application Security Testing (SAST) tools. While platforms like SonarQube have security features, these specialized tools are the true experts.
They are purpose-built to hunt down vulnerabilities like SQL injection, cross-site scripting (XSS), and insecure data handling with a much deeper level of analysis. SAST tools are all about helping teams "shift left" on security—embedding threat detection right from the beginning of the development process, not as an afterthought.
Comparison of Common Static Analysis Tools
To make sense of the options, it helps to see how some of the most popular tools stack up against each other. Each has its own strengths, so the "best" choice really depends on what you're trying to accomplish.
| Tool | Primary Languages | Key Focus (Security/Style/Bugs) | Integration |
|---|---|---|---|
| ESLint | JavaScript, TypeScript | Style, Bugs | Editor plugins, CI/CD pipelines |
| Pylint | Python | Style, Bugs | Editor plugins, CI/CD pipelines |
| SonarQube | 25+ languages (Java, C#) | Bugs, Security, Code Smells | CI servers, IDE integration |
| Checkmarx | 30+ languages (Java, C#) | Security (SAST) | CI/CD, IDEs, Bug Trackers |
| Snyk | JS, Java, Python, .NET | Security (SAST, Dependencies) | Git, CI/CD, IDEs |
| DeepSource | Python, Go, Ruby, JS | Bugs, Security, Performance | GitHub, GitLab, Bitbucket |
Ultimately, choosing the right static analysis tool is about matching its specialty to your project's most critical needs. Whether you start with a simple linter or go all-in with a comprehensive security platform, the goal is the same: to ship better, more reliable code.
Integrating Static Analysis into Your CI/CD Pipeline
Static analysis really shines when you don't have to think about it. The real magic happens when it becomes an invisible, automated part of your daily development work. We do this by weaving these powerful checks directly into the Continuous Integration/Continuous Deployment (CI/CD) pipeline, turning them from a chore into an automatic safety net.
This integration creates a tight, immediate feedback loop for developers. Instead of waiting for a teammate to spot a simple mistake during a manual review, the machine catches it first. This frees up human reviewers to focus on what they do best: tackling the bigger architectural and logical challenges. It’s a cornerstone of modern, efficient software development.
The Automated Quality Gate Workflow
When you plug static analysis into your CI/CD pipeline, you’re essentially creating what’s known as a quality gate. Think of it as an automated checkpoint that code must pass before it’s allowed to move to the next stage.
The workflow is beautifully simple yet incredibly effective:
- A Developer Pushes Code: A team member commits their changes and opens a pull request.
- The CI Server Triggers a Scan: That push automatically kicks off a build process on a CI server like GitHub Actions, Jenkins, or GitLab CI. As part of that process, the static analysis tool gets to work.
- Analysis Results Determine the Outcome: The tool scans the new code against its rule set and decides whether the build passes or fails.
If the scan finds something critical—like a major security vulnerability or a violation of a core coding standard—the build fails right there. The developer gets notified on the spot, and the flawed code is blocked from being merged. Just like that, the problem is stopped before it ever touches the main branch.
This quality gate approach does more than just catch bugs; it systematically enforces your team’s coding standards on every single commit. It ensures that every piece of code meets a minimum quality bar before it can be integrated.
This automated enforcement has driven a massive surge in market adoption. The global static analysis market was valued at approximately $1.59 billion in 2024 and is projected to climb to $1.85 billion in 2025. This growth is a direct result of its crucial role in DevOps and the increasing need for secure, compliant software. You can discover more insights about this accelerating market growth on OpenPR.
Empowering Developers with Immediate Feedback
One of the biggest wins from CI/CD integration is how it empowers developers. By giving them instant feedback, static analysis lets them fix issues while the context is still fresh in their minds. That’s far more efficient than finding out about a problem days later during a manual review.
This immediate loop doesn't just speed up development; it’s a continuous learning tool. When developers see their mistakes flagged in real-time, they naturally learn to avoid them in the future. Over time, this raises the skill level of the whole team, leading to a codebase that is cleaner, more secure, and easier to maintain. This consistent, automated process transforms static analysis from a simple tool into a core part of a high-performing engineering culture.
Best Practices for Making It Stick
Just dropping a static analysis tool into your workflow isn't the endgame. The real victory is weaving it so deeply into your team’s culture that it becomes an indispensable safety net, catching bugs before they ever see the light of day. To get there, you have to be smart about the rollout. The goal is to support your developers, not bury them.
A classic mistake is flipping every single rule on from day one. This almost always backfires, flooding developers with hundreds of warnings. It creates "alert fatigue," and before you know it, everyone's ignoring the tool's output entirely. A much better approach is to start small with a core set of critical rules. Zero in on the big stuff first—major bug patterns and security vulnerabilities.
Customize the Rules for Your Team
Once your team gets used to that initial, smaller ruleset, you can start tailoring it to match your own coding standards and priorities. Most static analysis tools are flexible, letting you enable, disable, or tweak rules to fit your project’s context. This is how a generic tool becomes your tool, enforcing what actually matters to your team.
It’s also crucial to bring that feedback directly to where your developers live: their Integrated Development Environment (IDE). An IDE integration means instant notifications, allowing developers to see and fix issues right as they’re typing. No context switching, no friction.
The moment you start treating static analysis alerts with the same seriousness as a failing unit test, everything changes. When an alert becomes a hard blocker for merging, the tool transforms from a background hum into a non-negotiable part of your quality process.
Get Ahead of False Positives
One of the biggest hurdles to getting your team on board is dealing with false positives. The static analysis market is growing fast, with cloud-based solutions making up 61% of deployments, but developer trust can be fragile. Some reports show an average of six false positives for every 1,000 lines of code, which can quickly erode confidence. If you want people to trust the tool, you have to manage these proactively. You can dive deeper into these trends in the full static code analysis market report.
To keep false positives from derailing your efforts, your team needs a clear plan for handling them:
- Triage and Suppress: Make it a habit to review flagged issues. When you find a genuine false positive, document why it's incorrect and configure the tool to ignore that specific instance in all future scans.
- Refine the Rules: Think of false positives as a learning opportunity. They show you where your ruleset might be a bit too aggressive for your codebase, giving you a chance to fine-tune it for better accuracy.
By following these practices, you can make sure your static analysis tool becomes a valued asset—one that consistently improves your code quality and strengthens your security posture, rather than just adding noise.
Common Questions About Static Analysis
When teams first dip their toes into static analysis, a few practical questions always seem to pop up. Getting clear on the answers helps separate the hype from reality, ensuring these tools become a welcome part of your workflow instead of just another source of noise.
One of the first hurdles is figuring out the difference between static analysis and linting. It's simpler than it sounds: linting is a specific type of static analysis. Think of it like this: all linting is static analysis, but not all static analysis is linting. Linting is your first-pass check, mostly focused on style, syntax errors, and making sure everyone on the team is following the same coding conventions. Broader static analysis tools go much deeper, hunting for complex bugs and security vulnerabilities that a linter would miss.
Augmenting Human Expertise
Another big question we hear is whether static analysis can just replace manual code reviews entirely. The answer is a hard no. What it does do is augment human review, making it way more efficient and valuable. Automated tools are brilliant at catching the routine, pattern-based mistakes that are easy for a human to miss after staring at a screen for hours.
This frees up your human reviewers to focus on what they do best: questioning architectural decisions, digging into the business logic, and assessing the overall design.
Static analysis acts as the first line of defense. It handles the repetitive, predictable checks so your developers can dedicate their brainpower to the creative, complex parts of a code review. This partnership between automation and human insight is where you get the highest-quality results.
Finally, teams inevitably wonder what to do with false positives. It’s a real issue—when a tool constantly flags things that aren't actually problems, people start ignoring it. The best approach is to have a clear process for dealing with these alerts. You can tune the tool's ruleset to better fit your codebase or use annotations to tell the tool, "Hey, we've checked this one, it's fine." This kind of continuous refinement is what turns the tool from a noisy distraction into an indispensable safety net for your code.
By automating code quality and security checks right inside your CI/CD pipeline, Mergify makes sure that only high-quality, secure code gets merged. Our merge queue and automation rules work hand-in-hand with static analysis tools to build a powerful, efficient development workflow. Discover how Mergify can streamline your code integration process.