Modern Enterprise Software Security Explained
When you hear the term "enterprise software security," what comes to mind? For many, it's firewalls, antivirus software, or maybe a final security scan before a product goes live. But that's an old, dangerously outdated picture.
Today, enterprise software security isn't just a lock on the door—it's the entire blueprint for a fortified digital city. It’s an organization-wide commitment to protecting the very systems that power your business, from your payroll software to your customer relationship management platforms.
This represents a huge shift in thinking. In the past, security was often an afterthought, something tacked on at the end. That model just doesn't work anymore. A single vulnerability in one application can ripple across your entire organization, leading to devastating data breaches, operational shutdowns, and severe damage to your bottom line and reputation.
The Shift to Proactive Defense
Modern enterprise security is built on a simple but powerful idea: be proactive, not reactive. The goal is to get ahead of threats by building defenses directly into the architecture of the software itself. It’s about anticipating weaknesses before they can be exploited.
This proactive approach rests on a few key principles:
- Zero Trust Architecture: This is the "never trust, always verify" mindset. It assumes threats can come from anywhere—inside or outside the network—so it demands strict identity verification for every single person and device trying to access resources. No exceptions.
- Security as Code: This practice means defining and managing your security policies using code. Think of it as creating automated, consistent, and repeatable security rules that are applied everywhere, every time, without manual intervention.
- Continuous Monitoring: Security isn't a one-time setup. It demands constant vigilance. You need systems that are always watching, ready to detect and respond to suspicious activity the moment it happens.
The financial stakes here are enormous, which is why we’re seeing such massive investment in this space. The global enterprise cyber security market was valued at around USD 55.24 billion in 2023 and is on track to more than double, hitting a projected USD 116.07 billion by 2032. This explosive growth makes one thing clear: businesses now recognize that solid security is a non-negotiable part of modern operations. You can dig into more of this data on IntelMarketResearch.com.
A strong enterprise software security posture does more than just stop attacks—it builds trust. Customers, partners, and employees need to know their data is safe. Security has become a cornerstone of your brand's reputation and long-term survival.
Ultimately, this modern approach sees security not as a roadblock to innovation but as its enabler. When security is embedded into every stage of development from the very beginning, you can move faster and with more confidence. You know your digital assets are protected from the ground up. This is the very bedrock of business resilience.
The Top Security Challenges Facing Modern Enterprises

The digital battlefield for businesses has never been more complicated. When you're building and maintaining enterprise software, you're not just fending off simple malware anymore. The threats are diverse, aggressive, and deeply intertwined with how we now build and deploy applications. These aren't just technical headaches; they're fundamental business risks that can halt operations, shatter customer trust, and lead to serious financial pain.
One of the most destructive threats out there is advanced ransomware. Forget the old screen-locking annoyances. Today's attacks are orchestrated by sophisticated groups who quietly infiltrate a network, spend weeks or even months mapping out critical systems, and then encrypt everything that matters. The whole organization grinds to a halt.
To make matters worse, these groups often use a double-extortion tactic. First, they demand a hefty ransom to unlock your data. Then, they threaten to leak the sensitive information they stole before they encrypted it, adding a whole new layer of pressure to pay up.
The Complexity of Cloud and Hybrid Environments
As companies have shifted away from traditional, on-premise data centers, they’ve walked into a new world of security headaches. Managing a sprawling multi-cloud and hybrid infrastructure is a massive undertaking. Instead of one well-defined perimeter to defend, security teams now have to protect assets scattered across various cloud providers like AWS and GCP, plus their own private servers.
This distributed setup creates a few major pain points:
- Inconsistent Security Policies: Trying to apply a single, uniform security standard across different cloud platforms is incredibly difficult. This almost always leads to gaps that attackers are quick to exploit.
- Visibility Gaps: It's tough to get a clear, unified view of all your assets and their activity. Threats can easily hide in the blind spots of a complex, fragmented network.
- Misconfiguration Risks: A simple human error while setting up a cloud service can expose mountains of sensitive data. In fact, misconfigurations are still one of the top causes of cloud-related breaches.
This growing complexity is precisely why the security market is booming. Enterprise data security is a huge piece of the larger cybersecurity puzzle, with projections showing the global market will soar to USD 98.5 billion by 2030. This growth isn't just a number; it's a direct response to the relentless need to defend data and networks from constant attack.
The modern security perimeter is no longer a solid wall; it's a fluid, shifting boundary defined by identity and access. Every user, device, and application is a potential entry point that must be continuously verified and secured.
Insider Threats and The Human Element
While external attackers get all the headlines, a surprising number of security incidents actually start from within. These insider threats can be malicious—think of a disgruntled employee stealing data on their way out. But more often, they're accidental, like a well-meaning developer who inadvertently exposes secret keys in a public code repository.
These accidental threats are everywhere. A developer might hardcode an API key into their application, push it to a public GitHub repository, and unknowingly hand an attacker the keys to the kingdom. It happens more than you think. This is exactly why it's so important to integrate automated secret scanning and enforce strict access controls.
To give a clearer picture, here's a quick breakdown of the core threats and where security teams need to focus their efforts.
Core Enterprise Security Threats and Mitigation Focus
| Threat Type | Primary Impact | Key Mitigation Focus |
|---|---|---|
| Advanced Ransomware | Operational disruption, data loss, financial extortion | Proactive threat hunting, immutable backups, incident response planning |
| Cloud Misconfiguration | Widespread data exposure, unauthorized access | Cloud Security Posture Management (CSPM), infrastructure-as-code (IaC) security |
| Insider Threats (Accidental) | Secret key exposure, intellectual property leaks | Automated secret scanning, Principle of Least Privilege (PoLP), developer security training |
| Software Supply Chain Attacks | Compromised dependencies, widespread system infection | Software Bill of Materials (SBOM), dependency scanning, secure build pipelines |
Ultimately, a strong defense requires a multi-layered approach. It's about combining smart technology with a culture that puts security first. Strong repository management is a critical piece of that puzzle, a topic we explore more deeply in our guide on GitHub security best practices.
How to Secure Your Software Supply Chain
Think of your finished software as a gourmet meal served at a five-star restaurant. Would you let your chef use ingredients from a questionable, unvetted supplier? Of course not. One bad ingredient could poison the whole dish.
This is the perfect way to think about your software supply chain—one of the most critical, and often overlooked, frontiers in modern enterprise software security.
Your software isn't built in a vacuum. It’s assembled from hundreds, sometimes thousands, of third-party libraries, open-source components, and vendor tools. Every one of these "ingredients" is a potential entry point for attackers. A vulnerability in just one small, obscure dependency can give bad actors a direct path into your entire digital ecosystem.
Understanding the Attack Surface
High-profile supply chain attacks have shown just how devastating a compromised component can be. When a popular library is infected, the malicious code can spread like wildfire to every organization that uses it. Suddenly, your own meticulously secured code is left vulnerable because the foundation it's built on is compromised.
This growing threat is exactly why the software supply chain security market has exploded. In 2025, this specific market is valued at USD 2.16 billion, with projections expecting it to grow to USD 3.27 billion by 2034. This investment highlights a clear industry consensus: you must know what's inside your software. You can find more insights on this growing market over at CustomMarketInsights.com.
The infographic below illustrates the core stages of a secure development lifecycle, which is fundamental to protecting that supply chain.
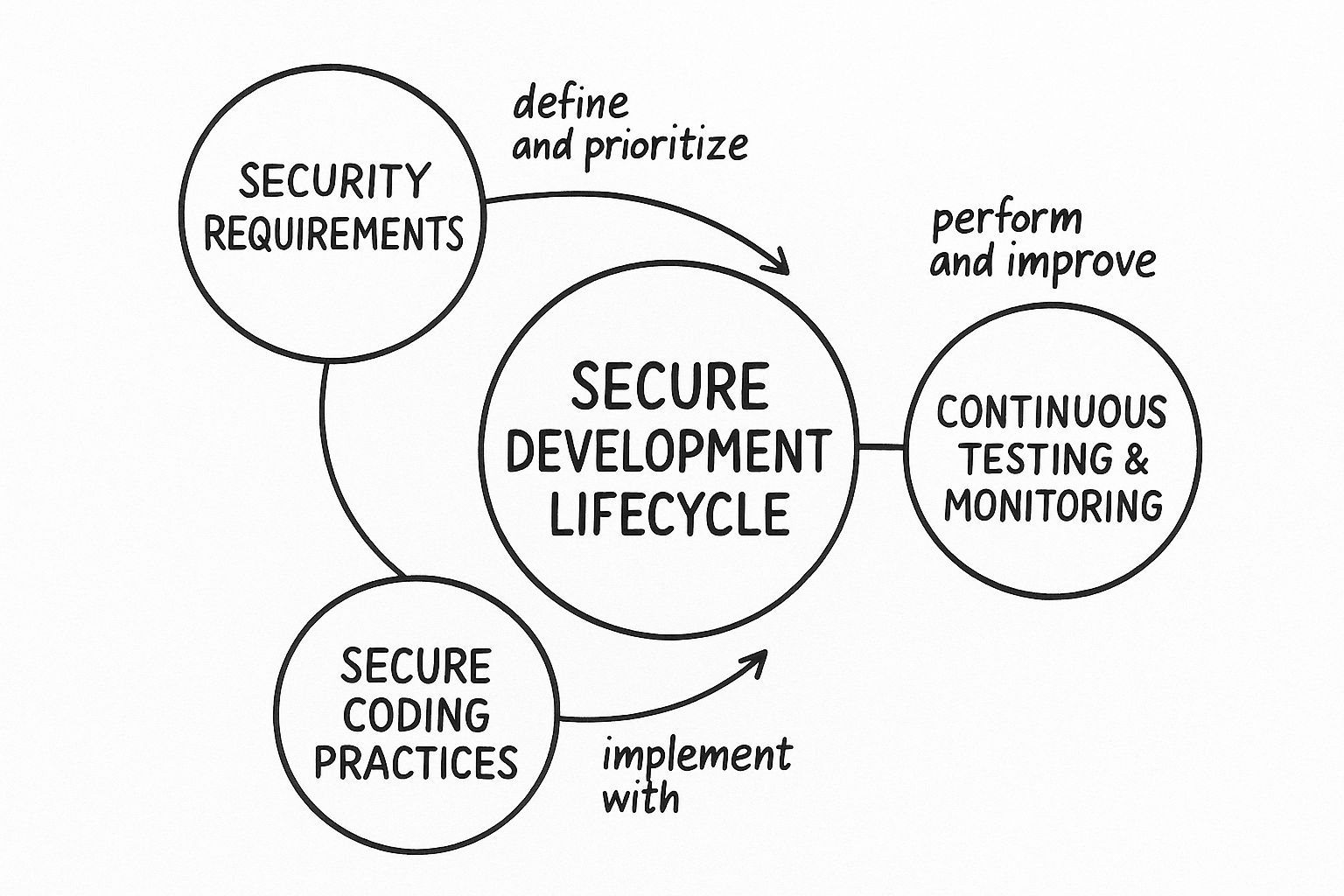
As you can see, it's a continuous loop—from setting security requirements and writing secure code to constantly testing the final product. It’s a cycle of reinforcement.
Building Your Defensive Strategy
Securing your software supply chain demands a proactive, multi-layered defense. You can't just cross your fingers and hope your dependencies are safe; you have to verify it. Here are the essential strategies to put in place:
- Create a Software Bill of Materials (SBOM): Think of an SBOM as the "ingredients list" for your application. It’s a formal, detailed inventory of every single component, library, and module used in your codebase. When a new vulnerability pops up in a common library, an SBOM lets you instantly pinpoint every affected application, enabling a fast and targeted response.
- Implement Continuous Dependency Scanning: Don't just scan once and call it a day. You need automated tools that continuously monitor your dependencies for known vulnerabilities. These tools should be baked right into your development pipeline to flag issues long before they ever dream of hitting production.
- Master Vendor Risk Management: Your responsibility doesn't stop with open-source code. You also have to rigorously assess the security posture of your commercial software vendors. That means reviewing their security practices, compliance certifications, and incident response plans.
The core principle of supply chain security is transparency. You cannot secure what you cannot see. The goal is to eliminate blind spots and gain complete visibility into every piece of code that makes up your final product.
Ultimately, these practices have to become part of your daily operations. Strong security needs a robust framework for integrating code and running checks efficiently. This is where automated merge queues and other CI tools become instrumental, ensuring that security scans and dependency checks are completed before any new code is integrated.
You can learn more by exploring our detailed guide on continuous integration best practices for modern teams. This approach turns your CI/CD pipeline into a powerful security gate, safeguarding your software from its very foundation.
Embedding Security Into Your CI/CD Pipeline
Traditional security models feel like having a single, overworked inspector at the very end of a factory assembly line. They check the final product for defects, but if they spot a problem, the entire line grinds to a halt. It’s slow, expensive, and turns the security team into a bottleneck—a source of friction nobody wants.
Modern enterprise software security flips this model on its head. It embeds security directly into the assembly line itself—your CI/CD pipeline. This is the whole idea behind DevSecOps: a cultural and technical shift that makes security an integral, automated part of how you build software, not just a final gate you have to pass through. It’s about building security in, not bolting it on at the end.
The goal is simple: answer security questions early and often. By integrating automated checks directly into the development workflow, teams catch vulnerabilities when they are tiny and easy to fix, long before they get tangled up in the codebase.
Shifting Security to the Left
You'll often hear the term "shifting left" in conversations about DevSecOps. It’s a simple but powerful concept. Imagine your development process as a timeline moving from left (writing the first line of code) to right (deploying to production). Shifting left just means moving security activities as far to the left—as early as possible—in that timeline.
Instead of waiting for a manual security review weeks after development is "done," automated security checks run every single time a developer commits code. This transforms security from a disruptive, periodic event into a continuous, quiet process humming along in the background. The result? Faster feedback, cheaper fixes, and a much more secure final product.
Shifting left isn't about turning developers into security experts overnight. It's about giving them the right tools and automated feedback to make secure choices effortlessly, right inside their existing workflow. The whole point is to make the secure path the easiest path.
This proactive approach is non-negotiable. We've all seen what happens when it's ignored. The recent widespread outage caused by a third-party security software update is a perfect example of how interconnected our software ecosystem is. As Microsoft noted during the CrowdStrike incident, this single event impacted 8.5 million Windows devices. It's a stark reminder of how deeply integrated third-party tools are and why securing the entire pipeline is so critical.
Key Security Tools for Your Pipeline
Weaving security into your CI/CD pipeline isn't just a philosophy; it requires a specific set of automated tools that give you immediate feedback. Here are the essential types of testing you should build into your workflow:
- Static Application Security Testing (SAST): Think of these tools as a spell-checker for your source code. They scan your code without ever running it, looking for common vulnerability patterns, coding mistakes, and security flaws. SAST is a true "shift left" tool because it can run on a developer's machine or as soon as code is committed.
- Dynamic Application Security Testing (DAST): If SAST inspects the blueprint, DAST crash-tests the finished building. These tools probe your running application from the outside, just like an attacker would. They search for vulnerabilities that only show up when the application is live, like injection flaws or server misconfigurations.
- Secret Scanning: This is absolutely non-negotiable for modern development. Secret scanners automatically search your entire codebase and commit history for exposed credentials like API keys, passwords, and security tokens. This simple step prevents accidental leaks that could hand attackers the keys to your kingdom.
- Software Composition Analysis (SCA): As we covered with the software supply chain, SCA tools are what generate your "ingredients list," or SBOM. They scan all your dependencies, identify every open-source library you're using, and check them against databases of known vulnerabilities.
Automating these checks creates a powerful, self-healing system. Of course, for teams looking to build robust workflows, optimizing the pipeline itself is a crucial first step. You can dig into some practical strategies in our guide on using Jenkins to optimize your CI/CD pipeline.
Ultimately, this automation empowers developers by giving them ownership. When a security scan flags an issue, the developer who wrote the code gets instant, actionable feedback. They can fix the problem on the spot, learn from the mistake, and help build a stronger security culture across the entire organization.
Actionable Best Practices For A Resilient Security Posture

Alright, you understand the threats and the importance of baking security into your pipeline from day one. That's the foundation. Now, let's get tactical and build on that with a playbook of best practices you can actually implement.
Think of it like building a fortress. A single thick wall is good, but it's not enough. A truly secure fortress has layers: high walls, a deep moat, vigilant watchtowers, and well-trained guards. Each layer complements the others. If an attacker somehow scales the wall, the moat is still there to stop them. This layered approach is exactly how you build a resilient enterprise software security posture that can withstand today's sophisticated attacks.
Enforce The Principle Of Least Privilege
The Principle of Least Privilege (PoLP) is one of the most powerful security concepts you can adopt, but it's shocking how often it's poorly implemented. The idea is simple: every user, application, and system component should only have the absolute minimum permissions needed to do its job. Nothing more.
Imagine giving the office janitor a master key that opens every single door—including the server room and the CEO's office. It’s completely unnecessary and introduces a massive risk. PoLP is about giving that janitor only the keys to the specific rooms they need to clean.
In the software world, this means a developer working on a front-end UI feature shouldn't have credentials that can access production databases. By enforcing this, you dramatically shrink your attack surface. If an account with limited access gets compromised, the potential damage is contained. The attacker can't move sideways through your network or access sensitive data because the account simply doesn't have the permissions.
Build A Zero Trust Architecture
The old "castle-and-moat" security model—where you implicitly trust everything inside your network—is officially broken. It’s a relic of a bygone era. Today, you have to operate on a completely different assumption: trust no one. This is the heart of a Zero Trust Architecture. It assumes threats can come from anywhere, both inside and outside your network perimeter.
The core mantra of Zero Trust is "never trust, always verify." It demands strict identity verification for every single person and device trying to access resources on your network, every single time, regardless of their location.
Putting Zero Trust into practice involves a few key moves:
- Strong Identity and Access Management (IAM): This is your new baseline. Using multi-factor authentication (MFA) is completely non-negotiable.
- Micro-segmentation: You break your network into tiny, isolated zones. If an attacker manages to get a foothold, they're trapped in a small segment and can't move freely.
- Continuous Monitoring: You have to actively watch all network traffic, constantly looking for anything that seems out of the ordinary.
This approach creates a far more granular and effective defense, where access is granted on a per-session, per-request basis—not based on outdated assumptions of trust.
Establish A Cadence Of Audits And Testing
You can't just set up your defenses and assume they're working. You have to kick the tires. You have to actively and aggressively test them. This is where regular security audits and penetration testing come in, giving you a much-needed reality check on your enterprise software security.
- Security Audits: Think of these as a systematic review of your security rulebook. Audits check your policies, controls, and procedures to make sure you're compliant with standards and, more importantly, that your team is actually following the rules you wrote down.
- Penetration Testing (Pen Testing): This is where the real fun begins. You hire ethical hackers to launch a simulated cyberattack against your systems. They'll find and exploit vulnerabilities, showing you exactly how a real-world attacker could break in.
Testing things regularly helps you find your weak spots before the bad guys do, giving you a chance to patch them up proactively.
Finally, you have to be ready for the day when something goes wrong. A comprehensive incident response plan is your playbook for when a security event happens. It needs to clearly spell out roles, responsibilities, and the exact steps to contain a breach, kick out the threat, and get your systems back online. A well-rehearsed plan is what separates a minor incident from a full-blown catastrophe.
Got Questions About Enterprise Security? We've Got Answers.
Even with a solid game plan, certain questions about enterprise software security always seem to pop up. Getting straight-up, practical answers is the best way to clear up confusion and get your team pointed in the right direction. Let's tackle some of the most common questions we hear from leaders and developers alike.
What’s the Very First Step to Improving Our Security?
Before you do anything else, you need to conduct a thorough risk assessment and asset inventory. It’s simple, really: you can't protect what you don't know you have. This means digging in and identifying every single piece of software humming away in your organization.
We're talking about everything from the applications your team builds in-house to the third-party services you pay for and, critically, all the open-source libraries your developers pull into their code. Once you have that complete list, you can start figuring out the potential vulnerabilities and business impact tied to each one. This gives you the clarity to put your resources where the biggest fires are, instead of wasting time and money on low-risk areas.
Your initial audit is your security roadmap. It shows you where your most valuable assets are and which roads are most likely to be attacked. Without it, you're driving blind.
How Is DevSecOps Different from Traditional Security?
Traditional security models are often stuck in their own silo, only showing up to run checks at the very end of the development cycle. It’s an old-school approach that almost always creates bottlenecks, turning the security team into a roadblock that slows down every release. Frankly, it's an inefficient and frustrating dance for everyone.
DevSecOps completely flips that script by weaving security into the entire DevOps lifecycle. It’s all about "shifting security left," which is a fancy way of saying we introduce automated security checks from the earliest stages of development. Suddenly, enterprise software security becomes a shared responsibility, not just one team's headache.
When you catch vulnerabilities early, they are far cheaper and easier to fix. The end result is a development process that’s not just faster and more consistent, but fundamentally more secure. Security stops being a brake and starts acting like an accelerator.
Why Is a Software Bill of Materials (SBOM) So Important?
Think of a Software Bill of Materials (SBOM) as a detailed ingredients list for your code. It’s a complete, formal inventory of every single component and library that makes up your applications. In today's world of tangled and complex software supply chains, its importance is impossible to overstate.
An SBOM delivers one thing above all else: transparency. When a massive, widespread vulnerability like the infamous Log4j incident hits the news, an SBOM lets you instantly pinpoint every single application in your portfolio that's affected.
This capability is an absolute game-changer for incident response. Instead of a panicked, all-hands-on-deck fire drill, you can launch a rapid, targeted fix. It dramatically shrinks your organization's exposure time to supply chain attacks and turns chaos into a structured, manageable process.
A secure and efficient development pipeline relies on smart automation. Mergify's Merge Queue ensures that every pull request is automatically updated and tested before it gets merged, preventing broken builds and keeping your codebase stable. By batching CI checks and enforcing security protections, Mergify helps you embed security directly into your workflow without sacrificing speed. Learn how Mergify can fortify your CI/CD pipeline.