GitHub Security – Best Practices to Protect Your Repositories and Metadata

Millions of open-source and commercial software projects use GitHub as their default hosting service, enabling developers from various locations to work together on shared codebases. Let’s look at the numbers: GitHub has recently announced that 100 million developers are now using the platform, making it an integral part of the DevOps workflow. And all users should remember that neglecting the aspects of Git security may lead to disastrous consequences, including data corruption and breaches, financial loss, reputational damage, and stock loss.
It is vital for the company to weigh all the risks connected to using GitHub. In this case, CISOs, CTOs, or DevOps/DevSecOps will be able to take preventive measures to mitigate such risks, save critical and sensitive information, and guarantee a continuous workflow.
Together with specialists from GitProtect.io, we've decided to figure out the best practices to protect your GitHub repositories and metadata. First, let’s look at the threats your GitHub can face and what responsibilities you have according to the GitHub Shared Responsibility model.
Step 1 – Understanding the Problem
🧐 What Can Go Wrong?
Outages, detected vulnerabilities and ransomware attacks could happen to any SaaS provider — GitHub is no exception. Just let us remind you about the most infamous GitHub-related incidents of 2022, including the Okta, Toyota, 0Auth, and Heroku cases with data breaches.
Just imagine: on average, the attackers may demand a ransom of around $570,000 for a single victim. And here we've just mentioned a ransom; now add to this the additional costs for downtime that can last approximately 20 days. Or what will you do if a threat actor refuses to give you back access to your GitHub data? Here is a threatening statistic: 99% of those who paid the ransom couldn't recover all their data without experiencing a loss.
➡️ GitHub Shared Responsibility Model
Like any other SaaS provider, GitHub operates within the Shared Responsibility Model, according to which GitHub and the user share the responsibilities over such aspects as storage, infrastructure, compliance, retention, and restoration.
To make a long story short, GitHub is a data processor whose obligations are to take care of the security of the cloud infrastructure, including the physical servers, network, and data centers. At the same time, the user is a data owner, which means that he needs to take care of the security of their application code and data, including access control, vulnerability management, and compliance. Let's look at the graphic to see the duties of both parties.
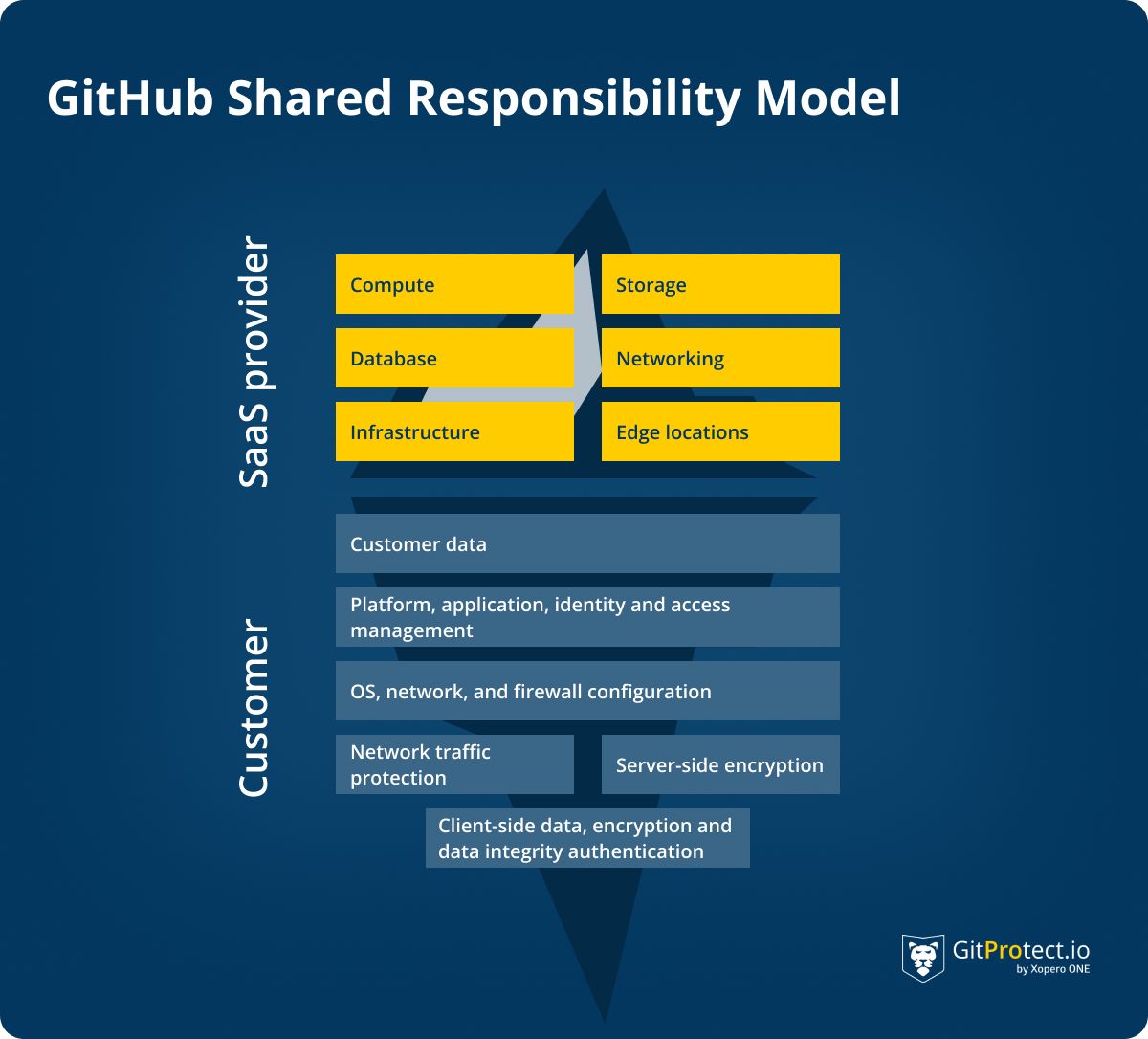
This model emphasizes the importance of collaboration and shared responsibility between GitHub and its customers to ensure the platform's security of applications and data.
➡️ GitHub Security Measures Described
All the abovementioned facts can make you think about what measures to take to improve your GitHub Security, eliminate drastic consequences (data loss, downtime, and budget expenditures), and have peace of mind. So, let's look at the most important aspects of enhancing your GitHub Security.
➡️ Code Scanning
Having frequent vulnerability and bug scans can help you feel more at ease because your DevOps team will be able to find and fix issues more quickly. For that purpose, you can use GitHub’s built-in code scanning function or third-party tools to scan, find, and fix issues in your development process. This way, you can prevent potential vulnerabilities from being exploited by criminals in the future.
We can't forget about secret scanning here to detect secrets, for example, keys and tokens, that have been checked into repositories. This way, you get notified about leaked credentials and immediately triage, revoke, or remediate them.
➡️ Access Control
The disclosure of credentials is considered one of the main causes of data breaches. That's why it's vitally important to be sure that those you grant access to your sensitive data. Here is worth mentioning the principle of least privilege (PoLP). Under this security concept, we understand that an employee has access to only that specific data, which is essential for completing his work.
Also, it’s preferable to use SAML SSO and IdP, which improves security and eliminates unauthorized access. To start their work, your DevOps must authenticate through your IdP to access your GitHub.
➡️ 2FA
Your password can be compromised and broken even if you consider it a secure and reliable one. From 8 to 15, unrelated lower- and upper-case letters, digits, and symbols can't guarantee that an attacker fails to break your password. However, you can strengthen your security with two-factor authentication with another layer of security - usually, code sent on your phone or app. Actually, by the end of 2023, 2FA will be a mandatory requirement for all GitHub accounts.
➡️ Merge Changes in a Controlled and Documented Way
Git merges and merge queue are not security features but are part of your GitHub security strategy for software development.
Git merge helps developers combine changes from multiple branches of code, which may further be used for collaboration and ensuring that different versions of a codebase are kept up to date. If DevOps merge the changes in their source code in a controlled and documented way, they can reduce the risk of introducing bugs or any other vulnerabilities in their code.
To manage the merging of code changes more systematically, you can use merge queues. With a centralized system for reviewing and approving merge requests, DevOps teams can ensure that changes are thoroughly tested and vetted before being added to the code base. Thus, developers can catch potential security issues before they make it into production. And there's no doubt that the automation in this process that Mergify provides can make your team much more productive because it permits your DevOps team to eliminate crucial but redundant tasks from their collective workload.
➡️ GitHub Backup and Recovery to Eliminate Data Loss
GitHub outages, ransomware attacks, human errors, or other failures are incidents that everybody can face. You can eliminate the consequences of the mentioned incidents with the help of regular backups. Just let's remind you that GitHub isn’t responsible for your data:

So to be sure that your GitHub data is accessible and recoverable from any point in time, you need to build a reliable backup strategy.
DevOps Backup - a GitHub Security Measure You Should Know
Let’s focus on GitHub backup as a security measure in detail: what options do you have?
🦾 Backup in Terms of the Shared Responsibility Model
We have already explained what the GitHub Shared Responsibility Model requires from both the service provider and customers. SaaS providers, as a rule, offer basic backup plans, usually including snapshots. Though we can't consider snapshots a reliable backup, snapshots only represent the state of the system at a certain point in time.
Another option is a manual backup. If a company decides to arrange a backup by itself, it needs to write a backup script, check its efficiency, check backup performance on a regular basis, and delete the repetitive data. In this case, the company may soon realize that such an option can’t satisfy the demands of the business since it's time-consuming and error-prone.
A next variant is a third-party tool, like GitProtect.io - GitHub backup available on GitHub Marketplace. In this case, you get automated backups and the assurance that all your backed-up data is accessible and recoverable from any point in time. Moreover, professional GitHub backup software will help you implement the 3-2-1 backup rule, which assumes that you have 3 backups kept in 2 different storages, and one of those storages is offsite.
🔍 DevOps Backup Explained - What to Consider When Choosing a Backup Software for GitHub
We have already mentioned that DevOps backup is one of the major security measures while you're building your GitHub security strategy. Let’s now look at the main features your backup should have to boost your company’s security and bring your DevOps team peace of mind:
- data to include in your GitHub backup: GitHub repositories and metadata, including wikis, issues, branches, LFS, pull requests, etc.
- choice of storage: a place where to keep your GitHub backups (cloud or locally)
- level of retention: unlimited retention to keep your data up to forever
- compliance with the 3-2-1 backup rule: you keep no less than 3 backup copies in at least 2 different storage locations, and 1 is offsite
- ransomware protection: immutable backups, WORM-compliant storage, and AES encryption with your own encryption key
- automated backups: set your own backup policy on schedule, rotate full, differential, and incremental copies, and manage it all in one central management console,
- set notifications: email, Slack notifications, advanced audit logs, and SLA reports to stay up to date
- Disaster Recovery Technology: possibility to have point-in-time restore, granular recovery of your GitHub repositories or only selected metadata, restore to the same or new repository or organization account (whether cloud or on-premise), restore to your local device, cross-over recovery when you recover your data from GitHub to GitLab or Bitbucket or migrate between platforms.

You can read more about GitHub Backup Best Practices in GitProtect.io’s blog post.
One More Thing… 🚀
When building your GitHub Security you shouldn't forget to evaluate and re-consider your security measures on a regular basis. It is important to analyze all your security efforts to ensure that you're on the right track to implement your GitHub environment's best protection. Make your data accessible and recoverable to mitigate any data loss risk. Try GitProtect.io for free