GitHub Security Best Practices
Managing a project on GitHub has its challenges. For many, mastering the entire Git workflow alone is enough to keep them busy for quite some time. However, beyond the basics of pulling, merging, commenting, and rebasing, super important security details loom like specters on the horizon, threatening to eradicate your codebase with little recourse left for restoration.
Getting up to speed with GitHub security best practices can help guarantee your project is protected from thieves, marauders, and malicious types at all times. We've put together a series of simple security steps followed by a few prime tips to take the security of your GitHub-based project to the next level. Take a look and implement each of the following ideas for tighter security and plenty of peace of mind.
Get your GitHub project secured 🔐
Securing your GitHub project involves juggling several tactics and processes, but don't worry! The steps below should set you on the right track toward stalwart GitHub defense and a super-secure codebase:
1. Practice safe credential management
Solid security practices start with simple concepts handled competently. Authentication is a seemingly simple practice handled many times over by multiple contributors to any given project on GitHub, yet it can be done incorrectly and put your entire codebase in jeopardy.
GitHub authentication via clients and the command line previously required that you submit your username and password to access certain features. This has since changed, and a more complex authentication flow is now mandatory across most of GitHub's services. The use of special access tokens is now standardized across the bulk of GitHub, making it necessary to leverage this security feature by default. However, storing and updating credentials can be complex, and various common development workarounds could lead to exposed tokens being harvested from your codebase or elsewhere. Credential managers help mitigate these risks by relieving developers of the burden of security feature implementation.
You can turn to OS-specific options such as wincred, osxkeychain, and GNOME keyring for single-factor authentication to simplify this essential security step. For developers in need of a consistent authentication process fit for use with remote shells, the official Git Credential Manager is a must.
Additional tactics worth exploring that closely align with a credential manager include activating sign-in alerts and using verified devices.
2. Leverage signed commits
GitHub opens up the process of contributing to a single codebase by design, but this superpower can prove to be a major weakness if left unchecked and undersecured. Commits to your codebase can come from many different people, and it may be necessary to keep track of them all to keep out malicious contributions. Commit signatures solve this dilemma by associating commits with an identity in a verifiable fashion.

By default, anyone can add an author to a commit, regardless of whether or not they’re the person being added. Not only is this messy, but it can also create a major compliance conundrum when an accurate audit trail is required for individual changes. You can use GPG (GNU Privacy Guard) to generate cryptographic keys that can later be used to verify your commits are authentic. GPG is also available for Windows and OSX, among other popular systems.
However, be aware that signed commits in GitHub do not guarantee that unsigned commits won't be merged, as we've discovered ourselves.
3. Review GitHub actions
Going over the GitHub actions associated with your project and your user account can help keep tabs on unwanted contributions and outright malicious actions taken by others that involve your codebase. GitHub provides a detailed security log to help enable this kind of review.
Searching the log is simplified with special operators, and a variety of options can be specified to filter out unwanted information. For instance, specific searches can be done based on operation type, repository, user, and action variety.
4. Implement pull request approvals
Setting branch-specific policies for pull requests can quickly cut down on vulnerabilities by requiring key team members to sign off on submitted changes to your codebase.
You can specify details such as a minimum number of reviewers approving each request before merging it into the main branch. This tactic is particularly powerful when used on release branches, as it keeps untested code from reaching end users unexpectedly.
Tips for better GitHub security 🦾
The following tips can help take your project's security on GitHub to the next level:
Use two-factor authentication
Two- or multi-factor authentication makes it much more difficult for nefarious types to take over your account by requiring additional access details. Although SMS options are discouraged, everything from physical security keys to time-based one-time password authentication apps is available for use on GitHub for this purpose.
Use a SECURITY.md file
A SECURITY.md file is a valuable standard to include in your project's repository. It is akin to a README.md file in that it provides quick access to important information about your project.
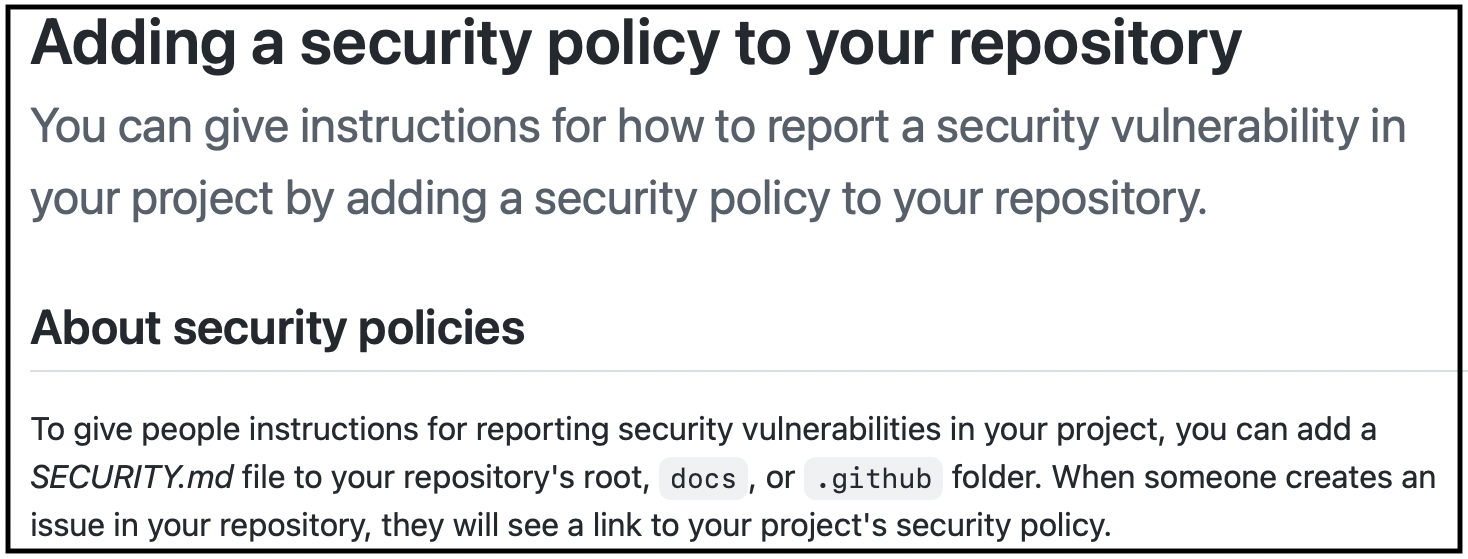
However, this file differs from others in that it makes carefully considering integral security details up front necessary for your team. A good SECURITY.md file contains the following:
- A disclosure policy to define the way issues and vulnerabilities should be reported;
- A security update policy that specifies how discovered vulnerabilities and bugs are expected to be handled, including the way code fixes will be delivered to users of your project;
- Known vulnerabilities and a general development roadmap users can anticipate from your codebase;
- Configuration best practices to enhance security when and where your code is utilized.
Need help with GitHub advanced security? 🖐
Implementing all of the security best practices covered above can effectively deal with the most common dangers inherent to open-source development through GitHub. However, many other security factors are worth considering to keep your repository safe from harm. For best results, it helps to have a helping hand.
Mergify can help 🥰
At Mergify, we take security seriously. We understand the importance of limiting access to critical files and branches, backing up important parts of your repository, and implementing predefined disaster recovery plans when compromised sensitive information. Reach out to our team if you need a competent security partner that can help keep your codebase secure 24/7.